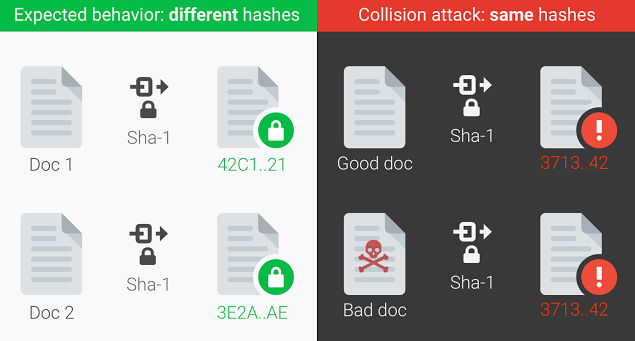
Well, SHA-1 encryption is used for HTTPS certificates which are right now used for protecting your browsing history and in Git repositories. SHA-1 encryption is used to prove that the data, whether it’s an email, passwords, PDF’s or any other credentials have not been interfered by the hacker of any kind. Now, the most horrific thing is Google has just managed to turn all these facts wrong by creating a hash collision. Google managed to alter a PDF without changing its SHA-1 hash value. This type of collision might force people into believing that the modified document was the original one. Google on its security blog wrote “Today, 10 years after of SHA-1 was first introduced, we are announcing the first practical technique for generating a collision. This represents the culmination of two years of research that sprung from a collaboration between the CWI Institute in Amsterdam and Google.” The entire effort was just to show tech community that SHA-1 encryption is now no more secure. Although Google always had depreciated SHA-1 for many years, especially when it comes to signing TLS certificates. Even, Google Chrome has been slowly phasing out the use of SHA-1 since 2014. Google security blog wrote “We hope our practical attack on SHA-1 will cement that the protocol should no longer be considered secure” and recommended the industry to move to the safer alternative like SHA-256. Well, now you all might be thinking how Google demonstrated the first ever SHA-1 Hash collision? Google had created two different PDF files that feature the same SHA1 hash and then used its cloud infrastructure to a computer the collision. Let me tell you Google had computed the collision which is one of the largest computations ever completed. According to Google Security Blog, here are some numbers that give a sense of how large scale this computation was:
Nine quintillion (9,223,372,036,854,775,808) SHA1 computations in total 6,500 years of CPU computation to complete the attack first phase 110 years of GPU computation to complete the second phase
Google had even mentioned that they would be disclosing the code after 90 days “Following Google’s vulnerability disclosure policy, we will wait 90 days before releasing code that allows anyone to create a pair of PDFs that hash to the same SHA-1 sum given two distinct images with some pre-conditions. In order to prevent this attack from active use, we’ve added protections for Gmail and GSuite users that detects our PDF collision technique.” Google has created a website to showcase the full attack. You can read the research paper. So, what do you think about this? Share your views in the comment box below.
Δ